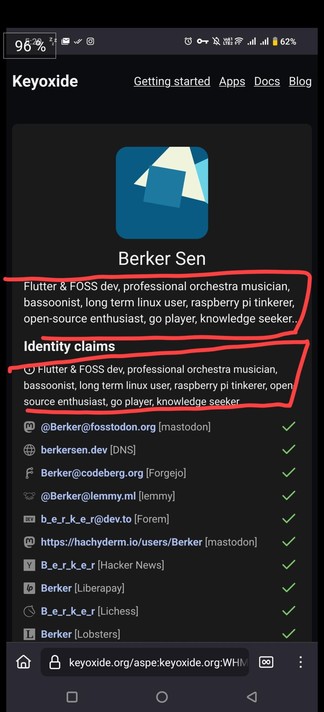
@aspensmonster @keyoxide @Berker Yes! That's good there's no need for two Keyoxide links (URL and the public key), I didn't know that. I'll try your guide later thanks. But you misunderstood me actually. I'm talking about the profile description inside the #Keyoxide page. When I type a description (it says optional) on the Android client, it shows up twice like this. Idk if it's a bug or supposed to be like that? Looks a bit weird having it repeated. (Berker is the Android client creator.)
Recent searches
Search options
#keyoxide
It is possible that Mastodon doesn't require a "proof", it just needs that <a rel
link right?
@shoppingtonz @a @keyoxide #keyoxide
A ha! I think I've found the problem. I created a test ASP profile on keyoxide with just this mastodon account as the claimed identity, done two different ways:
https://keyoxide.org/aspe:keyoxide.org:ZPZNQV5T2BDHSUVEFUINFRS4B4
The first way is the standard way of adding a claim to the ASP profile, by selecting the dropdown of "Mastodon" and putting in your username. This produces a `rel="me"` URL on the profile page that looks like this:
<a rel="me" href="https://tenforward.social/@aspensmonster" aria-label="link to profile">https://tenforward.social/@aspensmonster</a>
This follows the exact format that Mastodon docs say they are looking for in a verification link, and the Mastodon client will respect this and show the link as verified (see my "Keyoxide ASP" metadata block on my profile for proof).
However, if instead of "Mastodon" in the claim creation dropdown I pick "Manual input", and then put in a link to a specific *post* on my account as the claim, then the generated URL is instead:
<a rel="me" href="https://tenforward.social/users/aspensmonster" aria-label="link to profile">https://tenforward.social/users/aspensmonster</a>
Notice how instead of `$instance/@$user`, the format is `$instance/users/$user`. Since this is not what Mastodon expects the format of the verification URL to be, it does not show the URL as verified.
I believe that the `/users/` approach is a more general activitypub approach, and is probably more "AP standard." However, Mastodon specifically doesn't seem to consider that as equivalent.
Three options:
1. Mastodon accepts the /users/ approach and considers the link verified (probably won't happen)
2. Keyoxide tries to determine if the specific AP implementation is Mastodon, and tweaks the URL to be in the expected format (not ideal)
3. Have ASP users only use profile claims and not post claims for Mastodon if they want Mastodon's green checkmark (easiest).
For @shoppingtonz , the easiest thing for you to do would be to remove the post claim that you have on your ASP profile, and use the standard "Mastodon" dropdown instead. Then, the green verification bar and check should work for you too.
Test fiddling with #keyoxide asp passports.
Proof: https://keyoxide.org/aspe:keyoxide.org:ZPZNQV5T2BDHSUVEFUINFRS4B4
@aspensmonster do you know any guide for becoming verified on Mastodon through keyoxide?
I'm trying to figure out how to make the keyoxide.org appear as verified like it is on aspensmonster@tenforward.social.
I'm attaching an image so you don't have to visit the profile but you can see that my image and the profile both show the "verified" thing that Mastodon's system supports.
Do you know how we can make it green like shown in my attachment?
I never experienced KeyBase but I'm reading that
"Keybase is a key directory that maps social media identities to encryption keys in a publicly auditable manner."
For Mastodon this is BLISS!!!
I also read it supported chat n stuff...
KeyOxide manages the key directory stuff etc. and I've found the Android app to be fun to use and User Friendly!
I just linked two Mastodon accounts together! I'll do more soon!
@lynnesbian #keybase may be dead in the water, but #keyoxide is still around at least
@Xeniax Totally nerdsniped :D I'd love to be a part of the study.
I don't think that #KeyServers are dead. I think they evolved into Verifying Key Servers (VKS), like the one run by a few folks from the OpenPGP ecosystem at https://keys.openpgp.org/about . More generally, I believe that #PGP / #GPG / #OpenPGP retains important use-cases where accountability is prioritized, as contrasted with ecosystems (like #Matrix, #SignalMessenger) where deniability (and Perfect Forward Secrecy generally) is prioritized. Further, PGP can still serve to bootstrap those other ecosystems by way of signature notations (see the #KeyOxide project).
Ultimately, the needs of asynchronous and synchronous cryptographic systems are, at certain design points, mutually exclusive (in my amateur estimation, anyway). I don't think that implies that email encryption is somehow a dead-end or pointless. Email merely, by virtue of being an asynchronous protocol, cannot meaningfully offer PFS (or can it? Some smart people over at crypto.stackexchange.com seem to think there might be papers floating around that can get at it: https://crypto.stackexchange.com/questions/9268/is-asynchronous-perfect-forward-secrecy-possible).
To me, the killer feature of PGP is actually not encryption per se. It's certification, signatures, and authentication/authorization. I'm more concerned with "so-and-so definitely said/attested to this" than "i need to keep what so-and-so said strictly private/confidential forever and ever." What smaller countries like Croatia have done with #PKI leaves me green with envy.
Anyone here ever used the #keyoxide iOS app? How do you get your private key for a profile you create in it?
#keyoxide looks like a nice useful tool - any true benefits over a normal website? https://keyoxide.org
Introducing WKD Tester – a free, open-source tool for testing OpenPGP Web Key Directory implementations! I built it to help out with the Keyoxide project, making it easier to generate lookup URIs and discover keys on the fly. Check it out at https://wkd.chimbosonic.com.
@katzentratschen das war #Keybase und ist #Keyoxide heute...
Today I moved more services to the new infrastructure. Among them #Keyoxide and #Grafana (with #Telegraf and #Prometheus piggybacking).
#TIL: the localhost on the host is different from the localhost within a container. This can pose a challenge if you want to process from the host (via Telegraf or Node Exporter, as example) within the container.
It's true that there is a hostname that resolves to the host: host.containers.internal (for #Podman. #Docker has host.docker.internal)
But this is the public IP, i.e. the Internet exposed one.
Those magic hostnames could be used within prometheus.yml instead of localhost you tend to see there.
If you really need to access the host network, it would require to tear down the network isolation.
In other words: you have to pick a poison. I found an approach that is limiting the attack surface sufficiently low for my taste.
The remaining ones can be more challenging as they haven't been packaged for containers yet.
But that's something I wanted to learn anyway.
#gpg key expirations have been updated for another two-year bump. I also removed #twitter / X signature notation (I've deleted my account there), and added a bunch of other signature notations for other places I am online. It's making my #keyoxide page look dirty, but I intend to try and add support for as many of these as possible in the next few months.
Also, I updated my #tails #TailsOS installation while I was at it. I do most of my GPG key work from that environment.
@hyperreal From having implemented a #keyoxide claim verification service once, I can say that IRC and XMPP were far and away the most flaky endpoints to talk to, followed by Matrix. Ultimately, chat programs aren't really optimized for constantly serving up old messages at random (what Matrix claim verification does IIRC) and bots aren't always well-behaved (what IRC claim verification does IIRC). XMPP at least has the concept of storing non-message data (from some XEP or another; can't remember which) though.
Keybase is dead! Long live Keyoxide!
https://keyoxide.org/aspe%3Akeyoxide.org%3AGK4JFFYSVEI5NMLLGAXX22QZAU
Fingerprint: GK4JFFYSVEI5NMLLGAXX22QZAU
The workflow of creating an #Ariadne signature profile on @keyoxide is so much smoother than the #GPG equivalent! #keyoxide
• no looking up of command-line options
• no weird “notations”
• no exporting with --armor and copying .asc files
• no dealing with keyservers
You just fill in a couple input fields on https://asp.keyoxide.org & save your key somewhere. Done. I'd say #ASP would be a nice addition to @soatok's list of #PGP alternatives! https://soatok.blog/2024/11/15/what-to-use-instead-of-pgp/
https://keyoxide.org/aspe:keyoxide.org:CSY6CYWH443HWQ5LCB6IDQFWVU
You may have noticed that I updated my #Keyoxide profile link in various places. That was legit – my old RSA #OpenPGP key had expired back in early November without me noticing, and yesterday, I created a new #ed25519 key. If you still see my old Keyoxide link somewhere, please tell me. #pgp #rsa
https://keyoxide.org/FEF07E34F003F58EF486E744A49FCA80F5B7DE61
First, however, I had to manually update #GPG to version 2.4 by compiling it from source.
https://www.procustodibus.com/blog/2023/02/gpg-2-4-on-ubuntu-22-04/
QT https://fed.brid.gy/r/https://bsky.app/profile/did:plc:dxkyhpbv4bsktz3x2yp6m2rz/post/3lcvpgpgnu22j